Guardin’ Yer Treasure: A Pirate’s Guide to Power Platform DLP
- Tristan Danic

- Mar 10, 2025
- 5 min read
Ahoy, mateys! In the vast digital oceans of the Power Platform, your data be the treasure you guard with all your might. Data Loss Prevention (DLP) is yer trusted first mate in ensuring that sensitive booty doesn’t fall into the wrong hands. In this post, we’ll navigate the high seas of DLP! What it is, why it’s essential, and how to set up robust policies that keep your digital treasure safe from marauders.

What Be DLP in the Power Platform?
DLP in the Power Platform be a set of policies that control how data flows between different connectors (essentially, the channels that allow your apps and flows to communicate).
Just as a seasoned captain carefully monitors his crew’s actions, DLP ensures that data isn’t inadvertently shared with untrusted sources, protecting your treasure from unauthorized access.
Key Points:
Connector Classification: DLP policies categorize connectors into business and non-business groups. This prevents sensitive data from mixin’ with personal or unsecure apps.
Data Flow Restrictions: By setting rules, ye can control which connectors can work together, ensuring that only approved channels be used for critical data exchanges.
Risk Management: DLP minimizes the risk of data breaches, ensuring compliance with regulations and safeguarding your digital booty.
How to Chart Yer DLP Course
Implementing DLP in your Power Platform is akin to plotting a secure route through pirate-infested waters. Follow these steps to set up yer own DLP policies:
1. Assess Your Data Booty
Identify Sensitive Data: Determine which data be critical and requires extra guard.
Map Out Data Flows: Understand how data moves across your environment to pinpoint potential vulnerabilities.
2. Define Connector Groups
Business vs. Non-Business: Classify connectors into groups. Business connectors are trusted channels, while non-business connectors be restricted.
Establish Rules: Decide which groups can interact, ensuring that sensitive data remains in safe waters.
3. Implement the Policy in the Admin Center
Access the Power Platform Admin Center: Log in with your captain’s credentials.
Create a New DLP Policy: Configure the policy by selecting the appropriate connector groups and defining the allowed interactions.

When it comes to Data Loss Prevention (DLP) in the Power Platform, a well-structured naming convention is as crucial as a pirate’s map! It keeps yer policies organized, easy to manage, and prevents chaos from takin’ over yer ship!
⚓ Why be a proper naming convention so important?
Clarity & Consistency - A clear structure helps admins and makers quickly understand what each policy covers.
Scalability - As your fleet (organization) grows, a standard naming approach makes it easier to manage multiple policies across environments.
Enforcement & Governance - A consistent format ensures policies are applied correctly, avoidin’ loopholes that could sink your data security.
🏴☠️ Example Naming Conventions:
DLP_BusinessCritical_PRD - For policies governing mission-critical data in production.
DLP_RestrictedExternal_DEV - To block risky connectors in development.
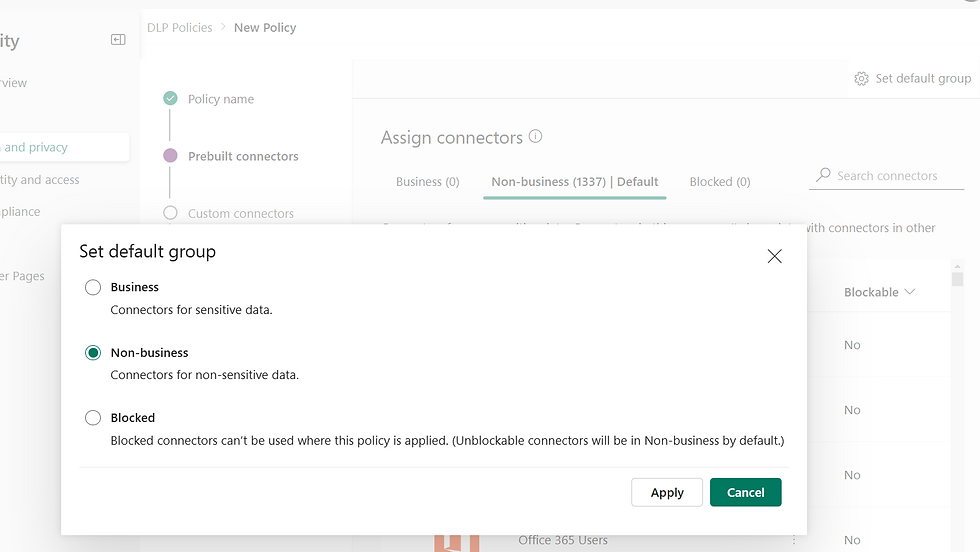
Ye can set the default group where any new connector be placed when it joins the fleet o’ available options! ⚓🏴☠️
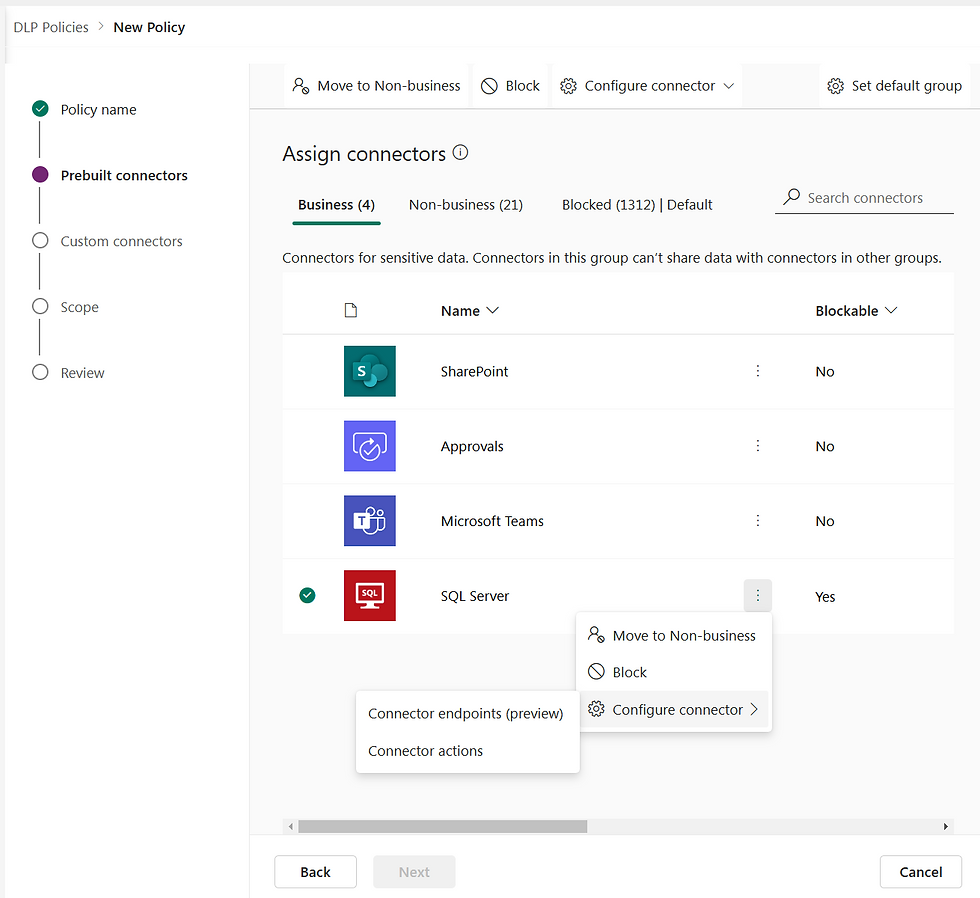
When settin’ up Data Loss Prevention (DLP) policies in the Power Platform, ye must chart yer course wisely by assignin’ connectors to three key groups:
🏴☠️ Business Group - This be the trusted part o’ yer fleet! Connectors in this group can freely interact with each other, makin’ it ideal for business-critical flows and apps. Example: SharePoint, Dataverse, Outlook (tools that keep the ship runnin’ smooth).
🏴☠️ Non-Business Group - These connectors be part of the crew, but they shouldn’t mingle with yer Business Group. This prevents data from spillin’ between regulated and unregulated systems. Example: Twitter, YouTube, Trello (useful, but ye don’t want ‘em mixin’ with sensitive business data).
☠️ Blocked Group - Arrr, these be the forbidden waters! Connectors in this group are completely restricted! No app or flow may use ‘em. Example: Personal email (Gmail), social media, public storage (lest ye want yer treasure floatin’ out to sea)!
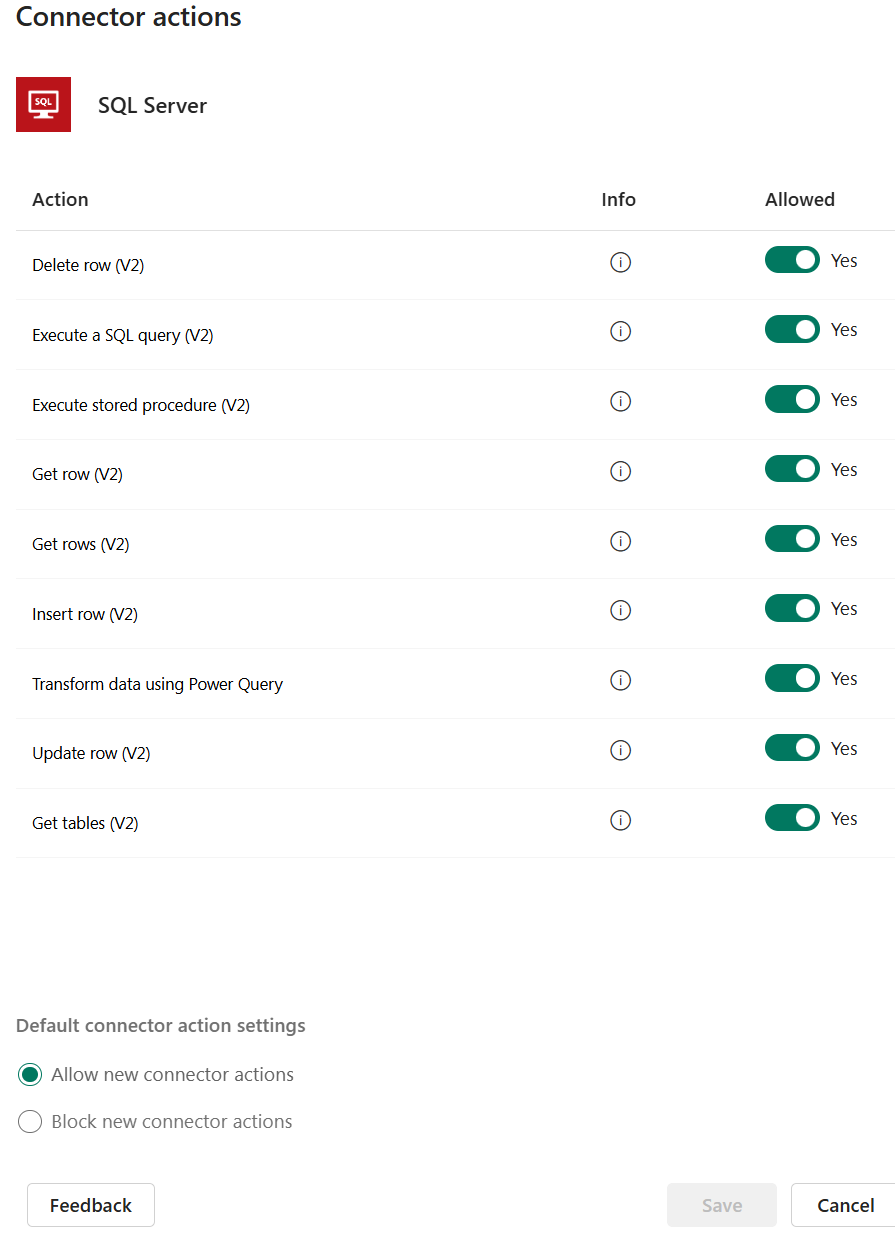
🏴☠️ Connector Actions - These be the commands ye give to a connector, like tellin’ a deckhand what to do. Actions can be:
Triggers - Kickstart a process when somethin’ happens (e.g., "When an email arrives" in Outlook).
Actions - Perform a task like sendin’ data, creatin’ a record, or fetchin’ information (e.g., "Create an item" in SharePoint).
BEWARE - Not every connector be setup!

🏴☠️ Endpoints - Think of these as the ports ye be communicatin’ with. Each connector sends requests to specific destinations. Some be internal harbors (Microsoft services like Dataverse), while others be risky open waters (external APIs, third-party services).
⚠️ Why does this matter for DLP?
Certain actions may expose sensitive data (ye must guard ‘em well)!
Some endpoints be safe business waters, while others be risky pirate coves (DLP policies help ye decide which ones yer crew can access).
Custom connectors be like buildin’ yer own secret passage in the Power Platform! 🏴☠️ They let ye connect to external systems using APIs when standard connectors won’t do the trick. But beware! Without proper DLP policies, these custom-built pathways could become open waters for data leaks, so be sure to assign ‘em to the right Business, Non-Business, or Blocked group to keep yer treasure safe! ⚓💀

When settin’ up Data Loss Prevention (DLP) in Power Platform, ye must choose the right scope to ensure yer policies apply where they be needed most. Here be the key differences:
🏴☠️ Add al environments - This be the broadest net, applyin’ yer DLP policies across the entire fleet (organization). No matter the environment, all makers must abide by these rules (perfect for keepin’ company-wide governance tight).
🏴☠️ Add multiple Environment - This scope applies to a specific environment, givin’ ye finer control. It lets ye set different policies for development, testing, and production environments, preventin’ rogue pirates from mixin’ sensitive data where they shouldn’t. 🏴☠️ Exclude certains Environment - ye can remove specific ones from the policy’s grip, givin’ ‘em more freedom.

Ye must hoist those environments into the DLP policy yerself if ye want 'em to sail under its protection!
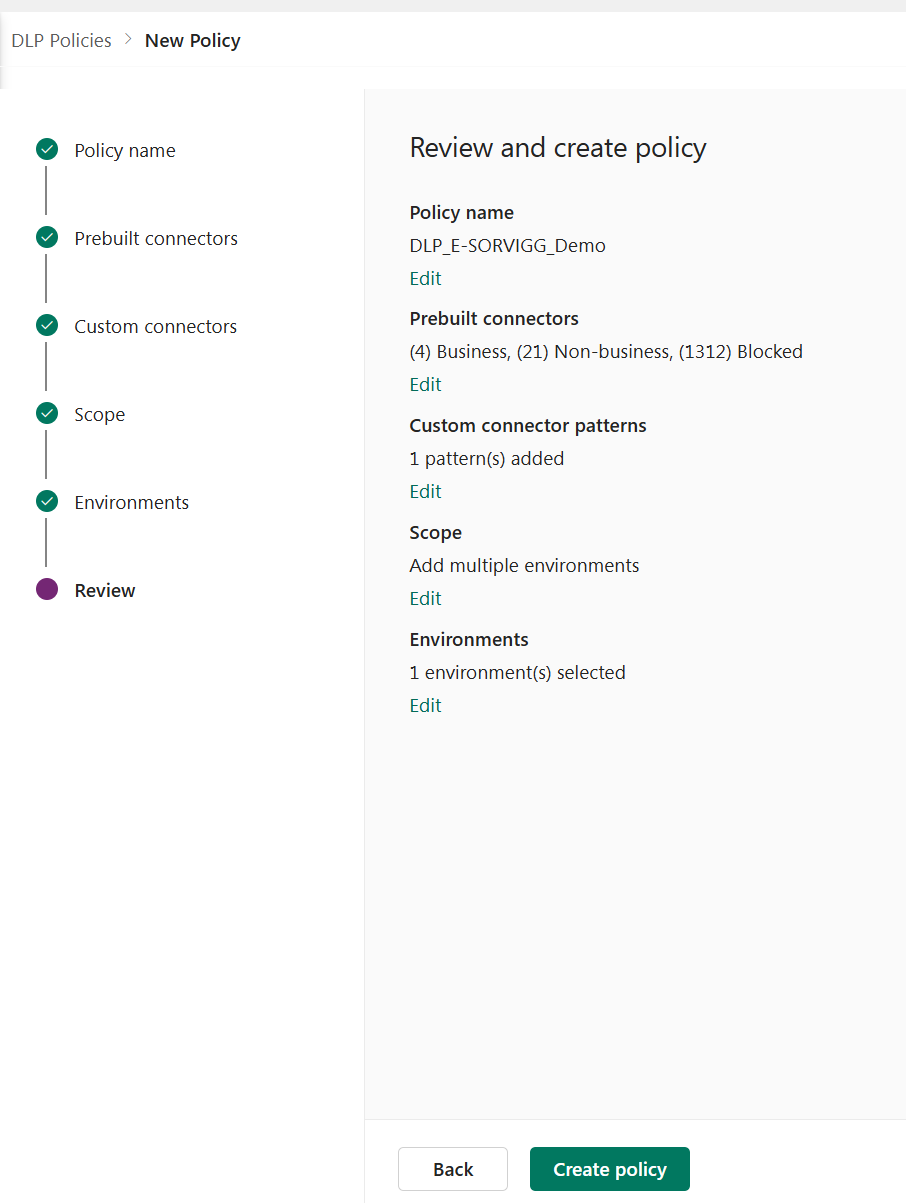
The final task be to give yer DLP policy a thorough once-over before settin’ it afloat! ⚓🏴☠️
Test the Waters: Run simulations to verify that the policy functions as intended without hampering legitimate business operations.
4. Monitor and Adjust
Regular Audits: Periodically review the DLP policies to ensure they adapt to new threats or changes in your environment.
Feedback Loop: Listen to your crew—your developers and administrators—for any issues or adjustments needed to maintain smooth operations.
Best Practices for DLP Mastery
Just as no pirate leaves his ship without proper maintenance, no organization should neglect the upkeep of its DLP policies. Here be some best practices to ensure your policies are as resilient as a well-anchored vessel:
Stay Informed: Keep up with updates from Microsoft regarding new connectors and changes in policy capabilities.
Educate Yer Crew: Ensure that everyone involved in the development and maintenance of your Power Platform is aware of DLP policies and understands the importance of data security.
Document Your Policies: Maintain thorough documentation of your DLP configurations and any changes made over time (this be your treasure map for future audits).
Automate Where Possible: Use automation tools to monitor data flows and trigger alerts for any unauthorized attempts to breach your DLP policies.
Conclusion
In the turbulent seas of digital transformation, safeguarding your data is paramount.
With robust DLP policies, you can ensure that your sensitive information remains secure—just like a treasure locked in a safe chest.
So, set your course with confidence, knowing that with the right DLP measures in place, your digital treasure is well-protected against any scallywags daring enough to try their luck.
Fair winds and secure data to all, mateys!
If ye be needin’ further guidance on navigating the Power Platform, don’t hesitate to drop anchor on my LinkedIn or send a message (I'm always ready to chart a course to safer shores).


Comments